Dnsmasq.
One thing that you home router provides is internet protocol addresses to every machine on the network with out you having to manually assign the ipaddresses (aka computer telephone numbers) to all the systems that request an address. It also associates hostnames for system connected to it like a telephone book. If for some reason your router fails, you can use an existing system to replace those services. You just need to install a software package known as Dnsmasq. In fact. that is the exact software most routers use to be a localize domain name services. You will want to use an extra nic so that later you can turn the system into a router.
From the Debian wiki.
Dnsmasq is a lightweight, easy to
configure, DNS forwarder and DHCP server. It is designed to provide DNS
and optionally, DHCP, to a small network. It can serve the names of
local machines which are not in the global DNS. The DHCP server
integrates with the DNS server and allows machines with DHCP-allocated
addresses to appear in the DNS with names configured either in each host
or in a central configuration file. Dnsmasq supports static and dynamic
DHCP leases and BOOTP/TFTP for network booting of diskless machines (source: from the package description).
Basic DNS setup
First things first, let’s install the package:
apt-get update apt-get install dnsmasq
If your goal was to set up a simple DNS server, you
just succeeded. To test it, use your favorite DNS lookup tool pointed at
localhost:
dig debian.org @localhost
or
nslookup debian.org localhost
By default, DNS is configured to forward all requests
to your system’s default DNS settings. In case you didn’t know, these
are stored in the /etc/resolv.conf file. See Debian Reference or the resolv.conf(5) man page for more details.
Now, if you want to add some names for your DNS server to resolve for your clients, simply add them to your /etc/hosts file.
Interfaces
One thing you will probably want to do is tell
dnsmasq which ethernet interface it can and cannot listen on, as we
really don’t want it listening on the internet. Around line 69 of the /etc/dnsmasq.conf file, you will see:
#interface=
Uncomment the line and specify which ethernet
interface(s) you want it server IPs to. For example, if I want it to
listen on eth1 (my DMZ) and eth2 (my local network), then it should look
like:
interface=eth1 interface=eth2
If I didn’t edit this line, it would also listen on
eth0, my internet connection. I personally wouldn’t recommend this, as
it gives those evil guys a few doors to try to break into.
Basic dhcp setup
By default, DHCP is turned off. This is a good thing,
as you could bring down whatever network you are connected to if you
are not careful.
To enable it, there is at least one line will need to edit in the /etc/dnsmasq.conf file. Around line 143, you will see: Make sure the existing network you are plugging into is not 192.168.0.x
#dhcp-range=192.168.0.50,192.168.0.150,12h
To enable the DHCP server, you will need to give it a range of IP addresses to hand out. In the example above, this server would hand out 101 address starting at 192.168.0.50 and ending at 192.168.0.150. The last number is how long the DHCP leases are good for. In this example, they would be good for twelve hours.
(Assuming he is using three nics and you are not
using an existing device using dnsmasq) Since I have two different
networks that need DHCP, I’m going to change that line to:
dhcp-range=eth1,192.168.100.100,192.168.100.199,4h dhcp-range=eth2,192.168.200.100,192.168.200.199,4h
Notice the “eth1″ and “eth2″ labels in the lines
above? The aren’t necessary, but definitely help once you start playing
with more advanced configurations. It also helps me remember which range
is which. Now restart your dnsmasq server, connect up a few clients,
and see if they autoconfigure themselves:
/etc/init.d/dnsmasq restart
Local caching
Using dnsmasq to cache DNS queries for the local
machine is a bit tricky, since all DNS queries from the local machine
need to go to dnsmasq, while as the same time, dnsmasq must be
configured to forward all those queries to upstream DNS servers.
-
 Do not use this configuration if you use different network (e.g If you use a laptop!)
Do not use this configuration if you use different network (e.g If you use a laptop!)
The dnsmasq(8) man page suggests the following:
- In order to configure dnsmasq to act as cache for the host on which it is running, put “nameserver 127.0.0.1″ in /etc/resolv.conf to force local processes to send queries to dnsmasq. Then either specify the upstream servers directly to dnsmasq using –server options or put their addresses real in another file, say /etc/resolv.dnsmasq and run dnsmasq with the -r /etc/resolv.dnsmasq option. This second technique allows for dynamic update of the server addresses by PPP or DHCP.
There is, however, a simpler method; simply ensure that the machine’s list of nameservers contains the line
nameserver 127.0.0.1
as the first line, followed by the upstream
nameservers. dnsmasq is smart enough to ignore this line and forward all
queries appropriately, while all other applications will send all their
queries to dnsmasq.
Exaclty how to do this depends on the method(s) of
network configuration in use. If you’re manually hardcoding the
nameservers (either in /etc/resolv.conf or elsewhere, such as a stanza in /etc/network/interfaces or in the Wicd GUI), then just add a reference to 127.0.0.1 as the first entry in the list. If you’re using DHCP, then instruct your client to prepend 127.0.0.1 to the DHCP servers it receives.
E.g., with dhclient, include the line
prepend domain-name-servers 127.0.0.1;
in the dhclient configuration file (/etc/dhcp3/dhclient.conf). [On my Sid system, the default configuration file shipped with the package contains that line, but commented out.] Note: that if you plan to use dnsmasq for the local system only, you should lock it down by adding the line
listen-address=127.0.0.1
to the dnsmasq configuration file (/etc/dnsmasq.conf).
—————————————
Debian gateway/router.
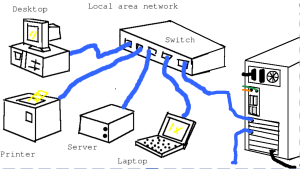
A multitude of reasons exist as to why one would want to build a custom router vs. suffer with the performance, reliability issues, and limitations of an off-the-shelf solution. What we are about to do is configure an incredibly fast and stable router/gateway solution for your home/office in about 15 minutes. (Note: This post assumes you already have your machine loaded up with a fresh copy of Debian and you have the two needed NICs installed. With systemd on the horizon, this setup will change. I would probably use auto instead of hotplug to configure the interfaces. First, let’s make three initial assumptions:
- eth0 is the public interface (the Cable/DSL modem is attached to this NIC)
- eth1 is the private interface (your switch is connected to this NIC)
- All of the client computers, servers, WAPs, etc. are connected to the switch
1.) Configure the network interfaces
Change the “address”, “netmask”, and “broadcast” values to match your internal network preferences.
nano -w /etc/network/interfaces # The external WAN interface (eth0) # auto eth0 allow-hotplug eth0 iface eth0 inet dhcp # The internal LAN interface (eth1) # auto eth1 allow-hotplug eth1 iface eth1 inet static address 192.168.0.1 netmask 255.255.255.0 network 192.168.0.0 broadcast 192.168.0.255
2. Install and configure DNSmasq
DNSmasq is DNS forwarder and DHCP server. Change “domain” to the FQDN of your network and “dhcp-range” to the desired range of DHCP addresses you would like your router to serve out to clients.
apt-get install dnsmasq
nano -w /etc/dnsmasq.conf interface=eth1 #not used this feature buy it might be a good idea. listen-address=127.0.0.1 domain=home.andreimatei.com dhcp-range=192.168.0.100,192.168.0.110,12h
3.) Enable IP Forwarding
Uncomment the following line:
nano -w /etc/sysctl.conf net.ipv4.ip_forward=1
4.) Configure iptables
We create a file called /etc/iptables.rules and put this rule set inside of it. As an example, this set includes allowing tcp traffic in from the outside world on port 222 (I run SSH on this alternate port) and also port-forwards tcp port 50,000 to an internal machine with the ip of 192.168.0.3. Use this as a guide for your own rules. This known as a firewall script. Use this or any other script at your own risk.
nano -w /etc/iptables.rules *nat -A PREROUTING -i eth0 -p tcp -m tcp --dpo rt 50000 -j DNAT --to-destination 192.168.0.3:50000 -A POSTROUTING -o eth0 -j MASQUERADE COMMIT *filter -A INPUT -i lo -j ACCEPT -A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT -A INPUT -i eth0 -p tcp -m tcp --dport 222 -j ACCEPT -A INPUT -i eth0 -j DROP -A FORWARD -i eth0 -p tcp -m tcp --dport 50000 -m state --state NEW -j ACCEPT COMMIT
5.) Activate your iptables rules
iptables-restore < /etc/iptables.rules
6.) Ensure iptables rules start on boot
Insert the following line into your /etc/network/interfaces file right underneath “iface lo inet loopback”
nano -w /etc/network/interfaces pre-up iptables-restore < /etc/iptables.rules
7.) Reboot and Verify
That’s it! After a reboot, you should now have a very basic Linux Router/Gateway for your network. This post obviously doesn’t cover some of the incredible additional flexibility which your new machine provides. I urge you to explore topics on traffic shaping, throughput monitoring, Intrusion Detection, and VPN configuration to learn how to harness the true power of running a dedicated machine as the central traffic cop of your network.
Other firewall scripts:
# if you don't have wget on your system, install it (on debian apt-get install wget)
wget http://robert.penz.name/files/firewall/iptables_firewall_scripts-0.3.tar.bz2
tar xjf iptables_firewall_scripts-0.3.tar.bz2
# if you get an error message you don't have the bzip2 installed --> install it
# (on debian apt-get install bzip2)Also see:
https://help.ubuntu.com/community/IptablesHowTo
http://www.perkin.org.uk/posts/iptables-script-for-debian-ubuntu.html
https://wiki.debian.org/Firewalls
https://wiki.debian.org/iptables
--------------------------------------------
Other notes:
# Configuration file for dnsmasq.
#
# Override the default route supplied by dnsmasq, which assumes the
# router is the same machine as the one running dnsmasq.
dhcp-option=3,192.168.1.1
# router is the same machine as the one running dnsmasq.
dhcp-option=3,192.168.1.1
# If you want dnsmasq to listen for DHCP and DNS requests only on
# specified interfaces (and the loopback) give the name of the
# interface (eg eth0) here.
# Repeat the line for more than one interface.
#interface=
interface="eth2"
# Set the DHCP server to authoritative mode. In this mode it will barge in
# and take over the lease for any client which broadcasts on the network,
# whether it has a record of the lease or not. This avoids long timeouts
# when a machine wakes up on a new network. DO NOT enable this if there's
# the slightest chance that you might end up accidentally configuring a DHCP
# server for your campus/company accidentally. The ISC server uses
# the same option, and this URL provides more information:
# http://www.isc.org/files/auth.html
dhcp-authoritative
# Uncomment this to enable the integrated DHCP server, you need
# to supply the range of addresses available for lease and optionally
# a lease time. If you have more than one network, you will need to
# repeat this for each network on which you want to supply DHCP
# service.
#dhcp-range=192.168.0.50,192.168.0.150,12h
dhcp-range=192.168.10.100,192.168.10.200,12h



Comments
Post a Comment