Is your network firewall backdoor open?
This is going to almost sound like a basis for a script from the old "Mission Impossible" TV show. First a little preparation. If you work for a company or have lots of computers where you live, most likely (at least I hope so) there is a device to control what comes into your network. In general this is called a network firewall. They are set up to keep the bad guys out from the outside. What they do not do is keep a control over what goes from inside to outside the network.
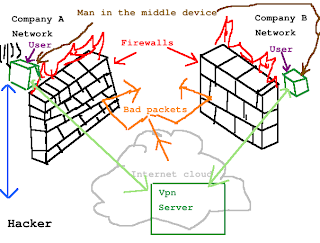
If persons or persons want access to your network, trying to get through a firewall is the hardest way in. If they could put a device on the inside of your network, then they have you lock stock and barrel. Somehow they get physical access to your facilities and install what is known as a man in the middle device. Your firewall at this point is now worthless.
Traditionally man in the middle devices were created from old wifi routers using modified firmware. Generally you had to be nearby to have access to those units. Today with the new embedded processors, they are so small that they can be hidden anywhere on the network. Only a trained eye, or a skilled network administrator can detect these devices.
Today, this same technique has become a lot more sophisticated. Persons wanting access to your network will usually rent or lease a third party server. With this server a connection from the man in the middle device is much easier. In most cases, they will set up a second man in the middle device at another location surreptitiously that also connects to the third party server. In fact is best done at a victim's competitors location so that it is more likely to be least detected and the competitor gets all the heat.
So the persons wanting access to your network do not have to be on the site of the competitor, a wifi (aka wireless) connection is used so everything can be monitored off-site. That means emails, passwords, documents, and general network traffic can all be monitored in safety, This s sometimes called sniffing.
Moral of the story. You need to physically monitor all internal network connections at desks, data closets, or anywhere there is access to the network. Make sure anyone working on the network is authorized to do so. Secondly, data going through the network has to be scrutenized also. One good way to see if there is a man in the middle attached some where is to disconnect the network at the desktop and see if there is still network traffic.
If there is, you will have to decide what to do next. You could disconnect it and then alert the persons and they will be gone immediately. Or you isolate that one network connection and set up what is known as a honey pot to keep their attention till the appropriate persons can be apprehended. One early good example of this, is documented in a book called "The Cuckoos Egg" by Cliff Stoll. In any case, you should alert the authorities immediately.
Note: I emailed (before the web as we know it today) back and forth with Cliff. He had some interesting things to say that were not included in the book.
If persons or persons want access to your network, trying to get through a firewall is the hardest way in. If they could put a device on the inside of your network, then they have you lock stock and barrel. Somehow they get physical access to your facilities and install what is known as a man in the middle device. Your firewall at this point is now worthless.
Traditionally man in the middle devices were created from old wifi routers using modified firmware. Generally you had to be nearby to have access to those units. Today with the new embedded processors, they are so small that they can be hidden anywhere on the network. Only a trained eye, or a skilled network administrator can detect these devices.
Today, this same technique has become a lot more sophisticated. Persons wanting access to your network will usually rent or lease a third party server. With this server a connection from the man in the middle device is much easier. In most cases, they will set up a second man in the middle device at another location surreptitiously that also connects to the third party server. In fact is best done at a victim's competitors location so that it is more likely to be least detected and the competitor gets all the heat.
So the persons wanting access to your network do not have to be on the site of the competitor, a wifi (aka wireless) connection is used so everything can be monitored off-site. That means emails, passwords, documents, and general network traffic can all be monitored in safety, This s sometimes called sniffing.
Moral of the story. You need to physically monitor all internal network connections at desks, data closets, or anywhere there is access to the network. Make sure anyone working on the network is authorized to do so. Secondly, data going through the network has to be scrutenized also. One good way to see if there is a man in the middle attached some where is to disconnect the network at the desktop and see if there is still network traffic.
If there is, you will have to decide what to do next. You could disconnect it and then alert the persons and they will be gone immediately. Or you isolate that one network connection and set up what is known as a honey pot to keep their attention till the appropriate persons can be apprehended. One early good example of this, is documented in a book called "The Cuckoos Egg" by Cliff Stoll. In any case, you should alert the authorities immediately.
Note: I emailed (before the web as we know it today) back and forth with Cliff. He had some interesting things to say that were not included in the book.


Comments
Post a Comment